The year 2020 has been an interesting twelve months to say the least with a majority of the workforce having at least some interaction with the virtual world. The COVID-19 pandemic has forced even some of our educators and students into an online learning environment. With more Americans online now than ever before, we are constantly exposing ourselves to cyber-attacks. Let’s dive into some quick tips and best practices for protecting what matters most – your data.
1. “PASSWORD123” IS NOT A PASSWORD
Complexity
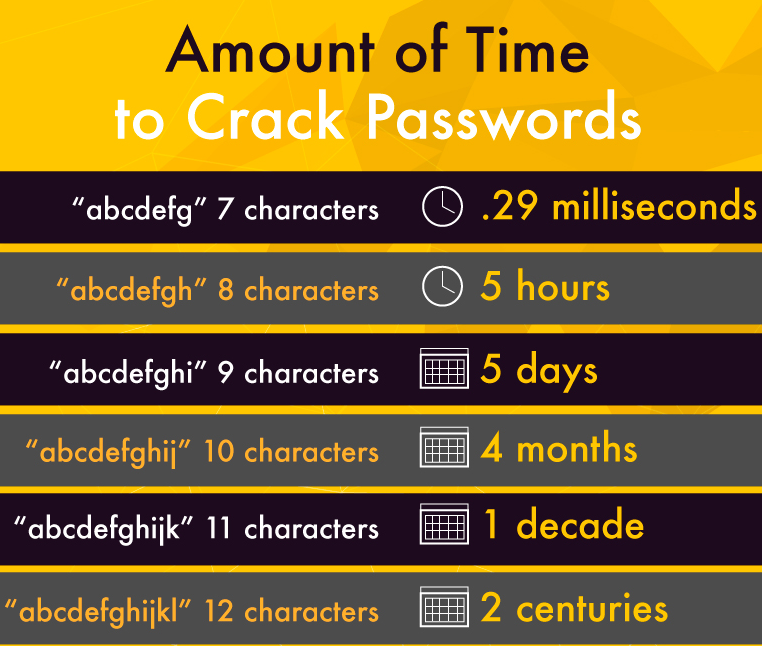
If you’re anything like the rest of us, you have a password you are comfortable with and most importantly can remember. It might be a favorite pet, your mother’s maiden name, or even your high school mascot. We could even venture to say that your password is probably almost the same (or slightly varying) for a majority of your logins. Little variation between passwords can make it easy for cyber criminals to guess your password and gain access to your information. This illustration below shows that the longer and more complex your password, the better.
Avoid using real words and/or personal information that would be easy to guess. An uppercase/lowercase mixture of alpha numeric characters is good. Adding in a special character is even better. Let’s look at the examples below.
 Weak: redfoxrocks
Weak: redfoxrocks
Better: RedFoxRocks
Good: RedFoxRocks1
Great: RedFoxRocks#1
Excellent: R3dF0xR@cKs#1
Time to Update
Passwords tend to weaken as time goes on. The best practice is to update or change your password at least every 90 days. Most applications and software have your password security in mind and should prompt you to update your password frequently. Remember, there are countless cyber criminals out there mining for your password and data – it’s best to keep them guessing.
Safe Storage
If you start making your passwords more complex, chances are at some point you will have a hard time remembering each one or will lock yourself out with too many failed login attempts. One way to avoid this is adopting a password-saving tool. Third-party tools such as LastPass, 1Password, and Dashlane allow users to safely store their passwords and avoid the need to remember all of their login credentials.
2. PHISHING FOR DATA
We all at some point (whether we knew it or not) have been on the receiving end of someone attempting to get personal information from us. Quite possibly it was disguised as a harmless email, or even a request from one of your favorite social media platforms. Identifying scams or phishing e-mails is an important step to protecting yourself from cybercrimes. Let’s look at a few things that might help us identify a scam.
- The request immediately discusses a need that can be filled only by you. Cyber criminals will try to pull at your heart strings while looking for information. Make sure when you read “We need donations” in the subject line that the e-mail is coming from a legitimate source.
- Unknown or faux sender – these can be tricky. Hackers have gotten good at disguising emails to look like the come from someone you know. Hover over the email address and make sure it’s one you recognize. If John Smith sent you an email as John1ax-eb$ts@bot.com be cautious. Call your sender if you are unsure. They could have been hacked and don’t even know it!
- Trapped in Spam or Junk – If it landed in your junk or spam folder, it’s probably for good reason. Be weary of allowing junk senders into your inbox unless you are sure the sender is real.
- Know how your financial institution communicates with you. Typically, we will never ask for personal identifiable information (PII) or sensitive information via email without a secure login portal.
A good rule of thumb – if you’re not comfortable with an email requesting personal information or something seems fishy, trust your gut and don’t respond or reach out to the sender personally to verify.
3. SHARED DRIVE: WHAT NOT TO SHARE
1. Physical Awareness – leaving a laptop or tablet unattended, storing passwords that are written down, and over the shoulder lookers are all things we should be aware of when protecting our information. Cyber attacks don’t always have to come to us virtually. Sometimes it could be the person sitting right next to you!
2. Private vs. Public – We all have our favorite coffee shop or café that is familiar to us and is a comfortable environment for us to study or get some work done. While their Wi-Fi is probably free, you cannot ensure that it is safe, and in most cases you should avoid connecting to public Wi-Fi. Personal hotspots and encrypted connections are great ways to help you safeguard yourself from the dangers of public Wi-Fi.
3. Keep Work at Work – private files from your personal computer could infect or cause issues to your work laptop, so it is best to keep things separate.
Conclusion
- Have updated antivirus/malware software monitoring and scanning your computer for vulnerabilities.
- Allow your computer time to update – Microsoft, Apple, and most of the other companies are constantly sending updates and patches to our machines in the form of updates. It may seem time consuming or pointless to restart your computer or schedule a time to allow it to update, but you may be doing more harm than good by delaying this process.
- Be aware of your surroundings, protect your passwords, and if in doubt, verify that an e-mail or digital prompt is legitimate.
You will never be 100% protected from hackers and cyber criminals, but there are things you can do to reduce your likelihood of a cybersecurity breach. You can have a number of protections and processes in place to operate safely in the virtual world, but the most important and first-line of defense is you!
https://www.betterbuys.com/estimating-password-cracking-times/
IMPORTANT DISCLOSURE INFORMATION: Past performance may not be indicative of future results. Different types of investments involve varying degrees of risk. Therefore, it should not be assumed that future performance of any specific investment or investment strategy (including the investments and/or investment strategies recommended and/or undertaken by BentOak Capital [“BentOak”]), or any non-investment related services, will be profitable, equal any historical performance level(s), be suitable for your portfolio or individual situation, or prove successful. BentOak is neither a law firm, nor a certified public accounting firm, and no portion of its services should be construed as legal or accounting advice. Moreover, you should not assume that any discussion or information contained in this document serves as the receipt of, or as a substitute for personalized investment advice from BentOak. Please remember that it remains your responsibility to advise BentOak, in writing, if there are any changes in your personal/financial situation or investment objectives for the purpose of reviewing/evaluating/revising our previous recommendations and/or services, or if you would like to impose, add, or to modify any reasonable restrictions to our investment advisory services. A copy of our current written disclosure Brochure discussing our advisory services and fees is available upon request at www.bentoakcapital.com/disclosure. The scope of the services to be provided depends upon the needs of the client and the terms of the engagement. Historical performance results for investment indices, benchmarks, and/or categories have been provided for general informational/comparison purposes only, and generally do not reflect the deduction of transaction and/or custodial charges, the deduction of an investment management fee, nor the impact of taxes, the incurrence of which would have the effect of decreasing historical performance results. It should not be assumed that your account holdings correspond directly to any comparative indices or categories. Please Also Note: (1) performance results do not reflect the impact of taxes; (2) comparative benchmarks/indices may be more or less volatile than your accounts; and, (3) a description of each comparative benchmark/index is available upon request. Please Note: Limitations: Neither rankings and/or recognitions by unaffiliated rating services, publications, media, or other organizations, nor the achievement of any designation, certification, or license should be construed by a client or prospective client as a guarantee that he/she will experience a certain level of results if BentOak is engaged, or continues to be engaged, to provide investment advisory services. Rankings published by magazines, and others, generally base their selections exclusively on information prepared and/or submitted by the recognized adviser. Rankings are generally limited to participating advisers (see link as to participation criteria/methodology, to the extent applicable). Unless expressly indicated to the contrary, BentOak did not pay a fee to be included on any such ranking. No ranking or recognition should be construed as a current or past endorsement of BentOak by any of its clients. ANY QUESTIONS: BentOak’s Chief Compliance Officer remains available to address any questions regarding rankings and/or recognitions, including the criteria used for any reflected ranking.